With SPF against spoofing and spam
E-mails with forged sender addresses are a tried and tested means for online criminals to send unwanted messages. The Sender Policy Framework (SPF) is designed to prevent such forgeries. Learn the technical background, how to configure SPF and how to perform an SPF check for your domains!
The Simple Mail Transfer Protocol (SMTP), as the basis for sending e-mails, does not inherently provide any security features to prevent the forgery of sender addresses. Attackers could therefore easily claim to be the legitimate sender of any e-mail address, which is also known as spoofing. If the originators of such messages distribute spam or junk mail with advertising content, this is merely annoying for the recipients. But in the case of phishing e-mails, which entice users with prepared attachments or links to disclose access data, theft and encryption of sensitive data as well as loss of reputation are the result.
SPF - Meaning
Fortunately, the threat of spoofing is steadily decreasing, because the SPF as an extension for SMTP makes it harder for attackers to find vulnerable email addresses the more companies secure their email domains accordingly. Nothing changes in the actual sending of e-mails via SMTP. Instead, SPF works at the level of the Domain Name System (DNS), i.e. the resolution of names to IP addresses.
SMTP has always relied on entries in the DNS, the so-called MX records (MX = Mail Exchange). If users want to send an e-mail to a specific destination address, their e-mail system uses the MX records to determine the servers responsible for the domain of the destination. SPF as a measure against spoofing extends this principle with new entries in the DNS, the SPF records. If administrators add an SPF record for each of their domains in the DNS, they can use it to define the IP addresses of the servers that are allowed to send e-mails for these domains.
When an e-mail message arrives, a receiving mail server checks whether an SPF record exists for its sender and, if so, whether the sending server is included in the list of permitted IP addresses. Depending on how strict the specifications of the SPF record are, the receiving system may reject the affected e-mail immediately (fail) or at least mark it as suspicious (softfail).
If no SPF record exists for a domain, mail servers typically accept messages, but even anti-spam systems, such as Gmail's, include SPF records in their risk assessment. Email addresses with configured SPF records usually receive a higher reputation and thus a significantly lower probability of being falsely declared as spam. Reason enough, therefore, to set up SPF Records for every company domain!
SPF Record Check
Once an SPF record is configured for a domain, the configuration can be checked in several ways. The Simple Email Reputation web service checks the settings of any email address, and the SPF Record Checker provides a more detailed evaluation of a domain's SPF record.
Users of Google Gmail have it even easier. They can simply click on the "Show original" option in the properties of an e-mail.
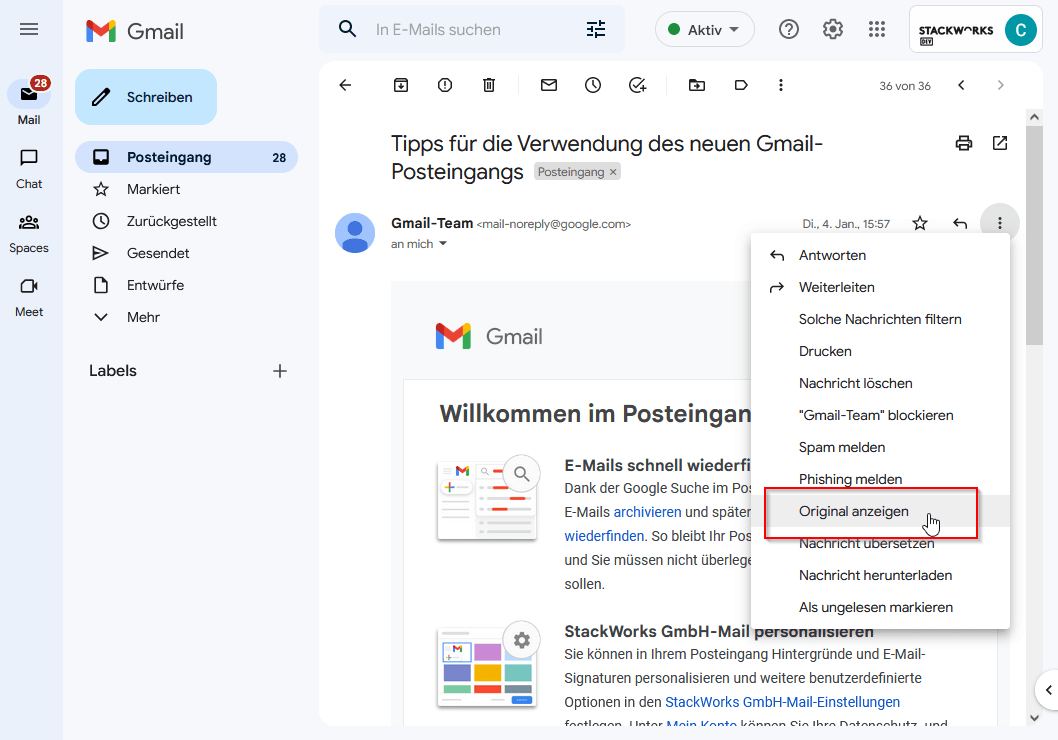
You will then see a detail view that shows whether the message passed the SPF check.
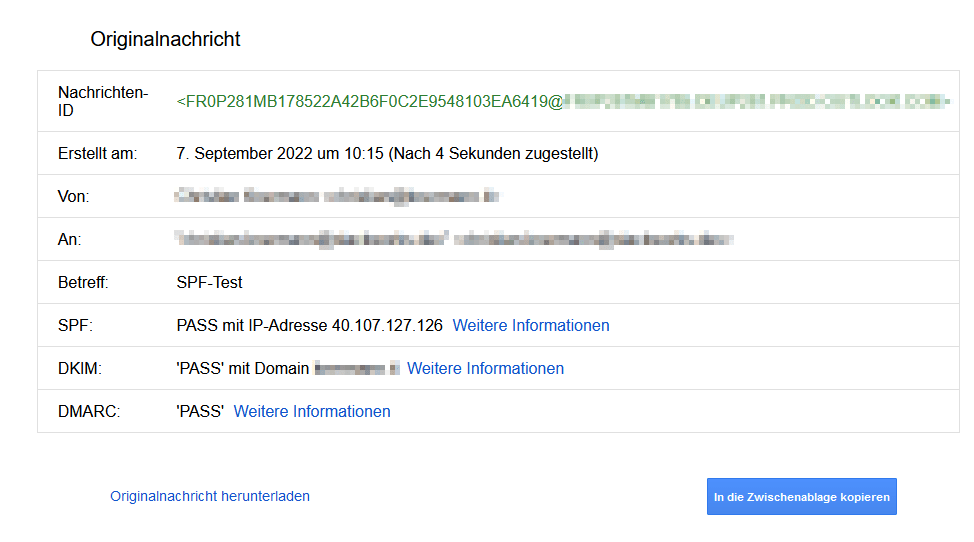
Google continues to test the additional technologies DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting and Conformance (DMARC). But how do you configure SPF for your domain?
Configure SPF Record
Various online services each provide an SPF generator, but configuring a suitable entry is easy even without such a generator. When selecting your e-mail provider, make sure that the provider provides the appropriate information!
In the case of Gmail, Google helps with a support article on how to set up a TXT record in your domain's DNS. If you already use Gmail, the value of a matching SPF record with the hostname "@" is either
v=spf1 include:_spf.google.com ~all
or
v=spf1 include:_spf.google.com -all
But what is the difference between these two entries? They instruct receiving mail servers to apply different strictness to the SPF check. The second instruction "-all" defines a hard fail, i.e. instructs the recipient to reject an e-mail if the SPF check fails. The entry "~all", on the other hand, corresponds to a soft fail, where the receiving mail server treats messages less strictly despite a failed SPF check and marks them as potential spam, but delivers them anyway. Our recommendation is to give preference to the fail. If you use other providers besides Gmail, e.g. for sending newsletters on behalf of your domain, you must also add their servers to the SPF record.
So protect yourself from spoofing and spam with SPF! Increase security and improve the reputation of your email addresses! We are happy to support you.